Data Governance – Data Privacy and Security – Part 1
Data Governance helps organizations manage their data effectively, ensuring quality and security for better decision-making.
Join the DZone community and get the full member experience.
Join For FreeIn every organization, there may be multiple source systems for various needs. Depending on how big the organization is, the source systems may vary from one to more than 1,000. Organizations often centralize their data in one place, integrate it, and derive value out of the data, such as a 360-degree view of customers, products, and so forth. To achieve this, a good data governance framework needs to be in place.
The Data Governance framework helps organizations to group the data in the appropriate way, manage the data, ensure the quality of the data, verify the consistency of data, and completeness of data, all to improve decision-making abilities and secure the data in an apt way.
The key pillars of Data Governance are described below. Data privacy and security are the two critical pillars for any product to be sustainable and successful.
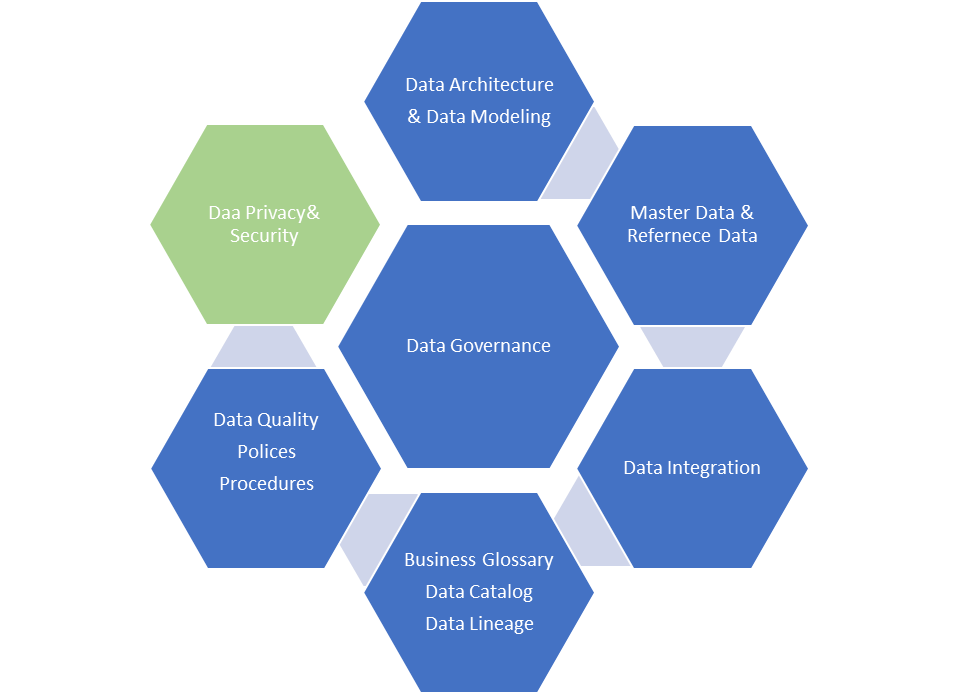
Data Privacy and Security
Data Privacy and Security could be implemented at the level of each individual system. However, when integrating data from different systems, a proper security framework must be implemented. Otherwise, the data may fall into a data privacy and security breach, which may cause a detrimental impact on the organizations. Here is the pictorial representation of data privacy and security.
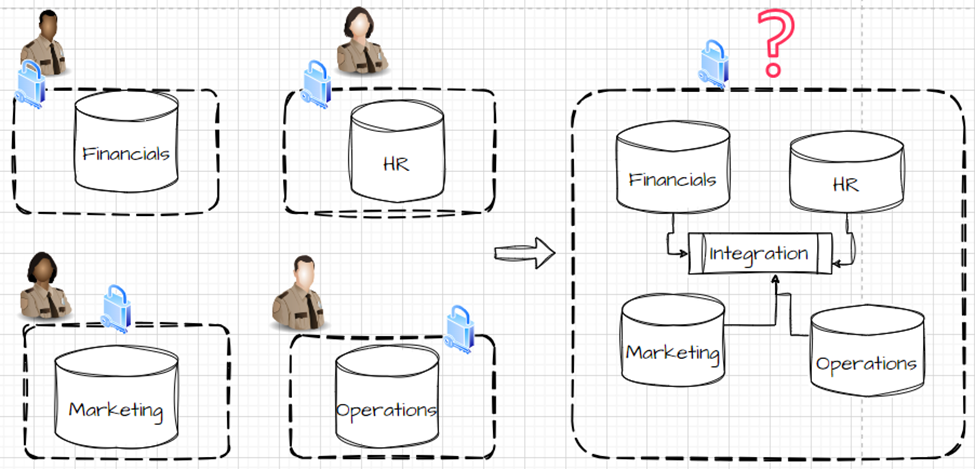
In the above picture, the individual systems, such as financials, HR, Marketing, and Operations, are secured individually. When the system is integrated into a centralized Datawarehouse location, there = challenges with security will arise.
Solution Approaches
To overcome those challenges with security in individual systems, there are predominately two ways: Authentication (Auth) and Authorization (AuthZ).
1. Authentication
Authentication is the process of verifying the identity of a user or process to get into the application or database, or any system.
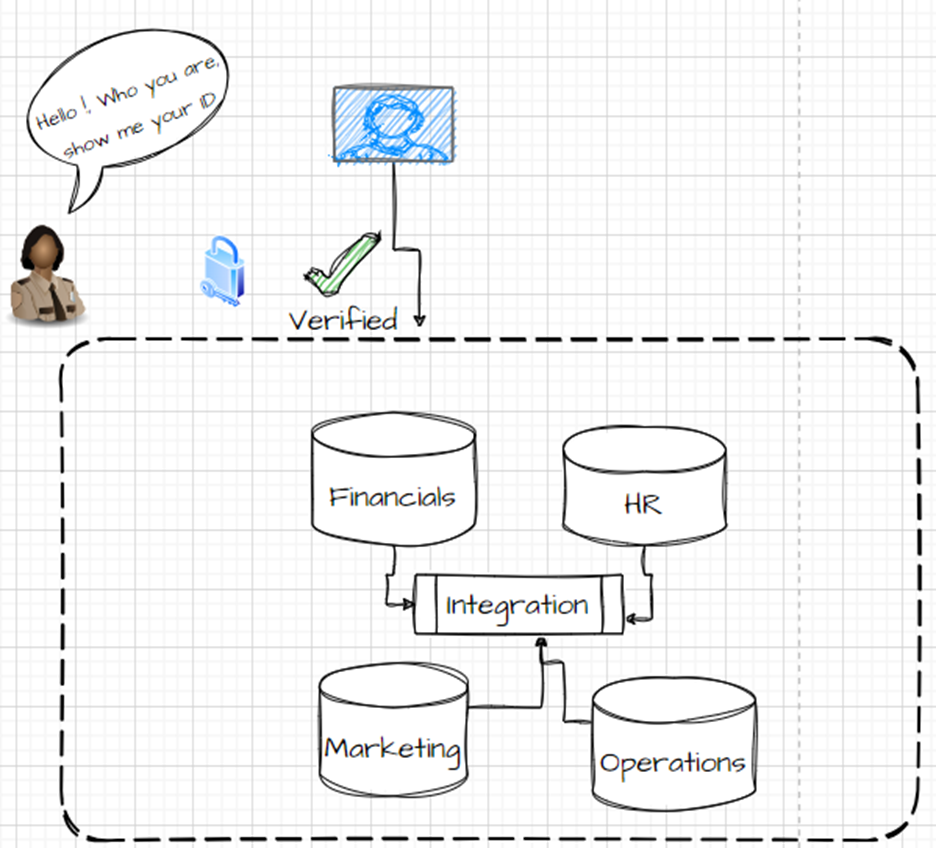
In database authentication modes, there are multiple ways to achieve it, but the prominent ones are:
- Password authentication (Example: SQL Server Authentication, Snowflake Database authentication)
- Windows Integrated Authentication
- Active Directory (LDAP)
- SSO (Single Sign On authentication)
- Key pair authentication
- Certificate-based
- MFA
2. Authorization
Authorization is the process where the authenticated user is allowed to access the different objects, their data, and the different operations a user can perform; for example, the user is allowed to read only some set of records or some set of attributes only, and the user can only perform update or delete operation on some set of data.
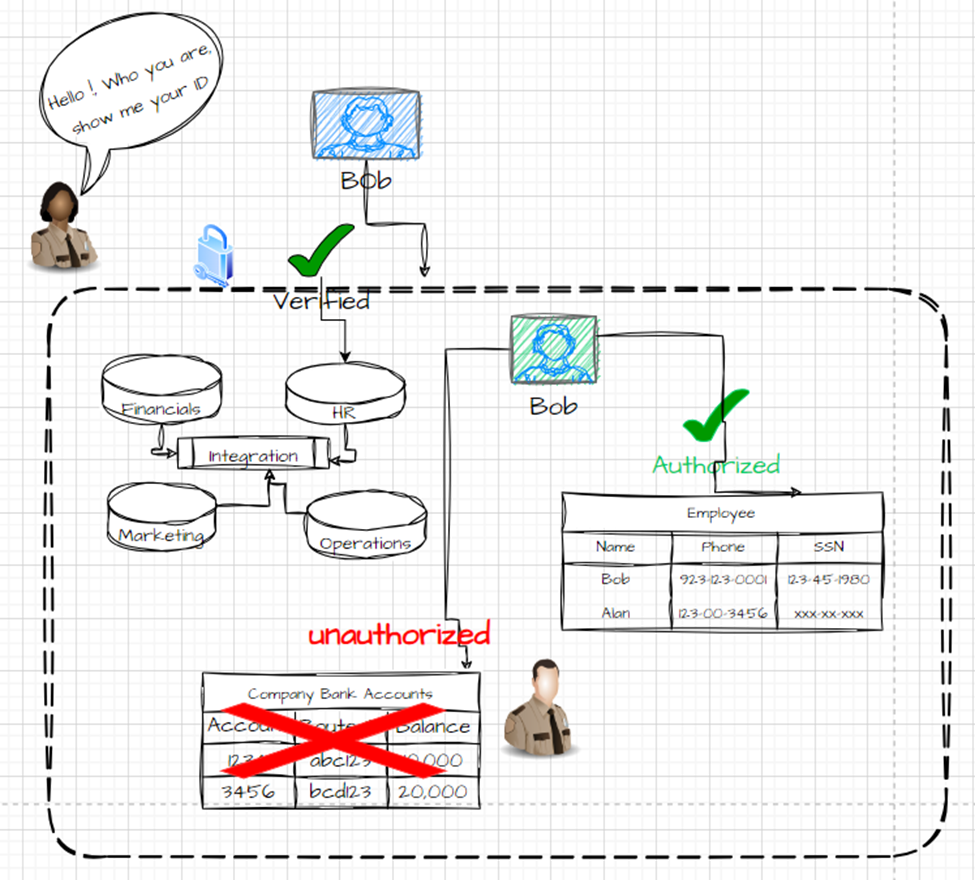
There are several types of data authorization methods. The six prominent ones are Role Based Authorization and User-based Authorization. Depending upon the application’s security complexity, other methods also can be implemented, such as Attribute-Based Authorization, Attribute Based Access Control, Context-Based Authorization, and Rule-based Authorization.
Below, I will briefly describe Role-Based Authorization and User-based Authorization.
Role-Based Authorization: In this type of Authorization, the objects and the data security are assigned to the roles, and the users are then assigned to roles.
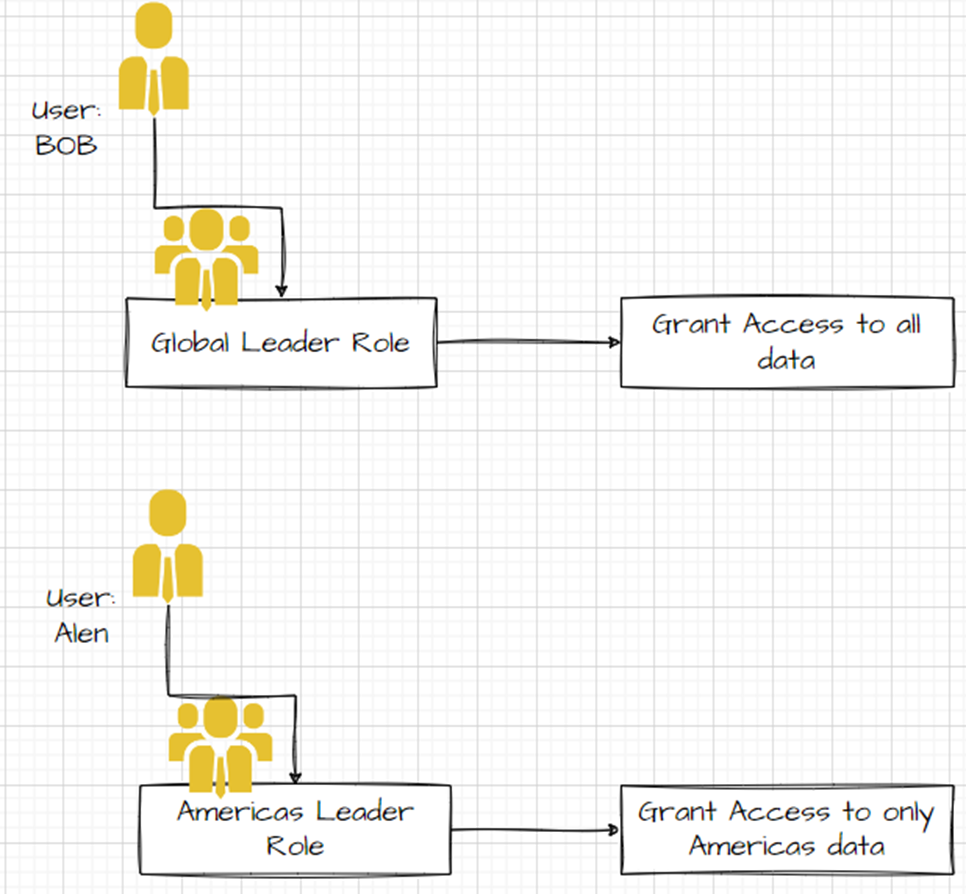
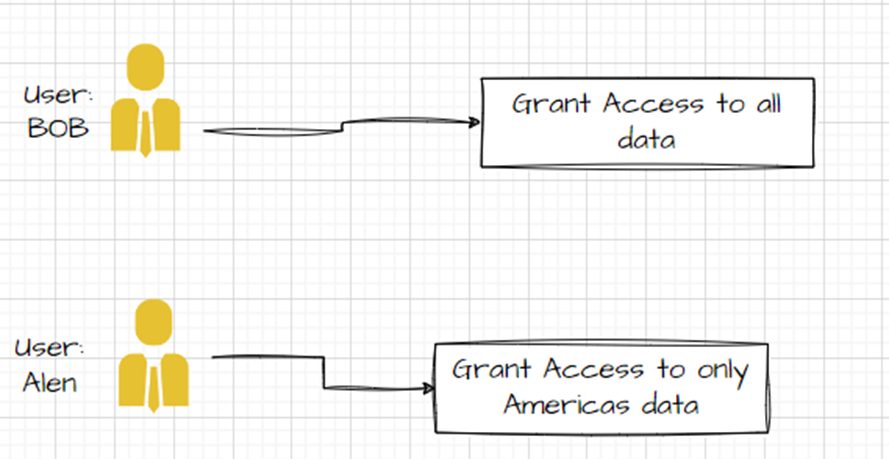
User-Based Authorization: In this type of Authorisation, the objects and the data security will be assigned to individual users, and the users are given grants to the database objects and the data.
Conclusion
The key takeaways from this article are:
- A robust data governance framework is needed when we integrate data from various source systems.
- Within data governance, data privacy and security are vital components to account for.
- Data privacy and security can be implemented at an individual system level; however, when we bring all the source system data into a centralized location causes, security and data breach concerns arise.
- Authentication and Authorization are two main ways to strengthen the data governance framework.
Opinions expressed by DZone contributors are their own.

Comments