DLP: AI-Based Approach
This article briefly talks about the AI-based approach to Data Loss Prevention (DLP) strategies. AI offers several advantages over traditional approaches.
Join the DZone community and get the full member experience.
Join For FreeDLP, or Data Loss Prevention, is a proactive approach and set of technologies designed to safeguard sensitive information from unauthorized access, sharing, or theft within an organization. Its primary goal is to prevent data breaches and leaks by monitoring, detecting, and controlling the flow of data across networks, endpoints, and storage systems.
DLP solutions employ a variety of techniques to achieve their objectives:
Content Inspection
DLP systems inspect data in motion, at rest, or in use to identify sensitive information such as personally identifiable information (PII), intellectual property, financial data, or confidential documents. They analyze content based on predefined policies and rules, which can include keywords, regular expressions, data fingerprints, and data classification tags.
Policy Enforcement
Organizations can define and enforce policies that dictate how sensitive data should be handled and protected. These policies specify actions to be taken when sensitive data is detected, such as encryption, quarantining, blocking transmission, alerting security personnel, or applying digital rights management (DRM) controls.
Contextual Awareness
DLP systems take into account the context surrounding data usage, including user identity, device type, location, time of access, and intended recipients. By considering contextual factors, DLP solutions can apply appropriate security measures and mitigate risks more effectively.
Discovery and Classification
DLP tools assist organizations in identifying and classifying sensitive data across their IT infrastructure. They help discover data stored in various repositories, including databases, file shares, cloud storage, and endpoints. Classification enables organizations to prioritize protection efforts and allocate resources more efficiently.
Monitoring and Reporting
DLP solutions continuously monitor data transactions and generate comprehensive reports on data usage, policy violations, security incidents, and compliance status. These reports provide valuable insights into security posture, help organizations assess risks, and facilitate regulatory compliance audits.
Integration With Security Ecosystem
DLP solutions often integrate with other security technologies such as firewalls, intrusion detection systems (IDS), identity and access management (IAM) platforms, and security information and event management (SIEM) systems. Integration enhances overall security posture and enables coordinated responses to security events.
AI Approach
This particular section of the article talks about content inspection using AI. AI offers several advantages compared to traditional methods for DLP.
Accuracy and Precision
AI-driven content inspection algorithms can analyze large volumes of data with higher accuracy and precision compared to manual or rule-based approaches. AI can identify sensitive information based on context, semantics, and patterns, enabling more effective detection of data leakage and policy violations.
Scalability
AI-powered content inspection solutions can scale to handle the growing volume and complexity of data across enterprise systems. Traditional methods may struggle to cope with the scale of modern data environments, leading to incomplete or inefficient content inspection processes.
Automation
AI automates the content inspection process, reducing the need for manual intervention and human error. AI algorithms can continuously scan and analyze data transmissions in real time, enabling organizations to enforce data protection policies more effectively without impacting productivity.
Adaptability
AI-driven content inspection solutions can adapt and evolve over time to address new threats, regulatory requirements, and business needs. Unlike static rule-based systems, AI algorithms can learn from past incidents and update their detection capabilities to detect emerging patterns and anomalies.
Complexity Handling
AI can handle the complexity of modern data formats, structures, and languages more effectively than traditional methods. AI algorithms can parse and understand unstructured data such as text, images, and multimedia content, enabling comprehensive content inspection across diverse data sources.
Reduced False Positives
AI algorithms can reduce false positives by contextualizing data inspection results and correlating multiple data attributes. By considering factors such as user behavior, access patterns, and data sensitivity, AI can prioritize alerts and focus on high-risk incidents, minimizing the burden on security teams.
Continuous Learning
AI-driven content inspection solutions can continuously learn and improve their detection capabilities over time. By analyzing feedback from security analysts and incorporating new threat intelligence data, AI algorithms can enhance their accuracy and effectiveness in detecting data leakage and policy violations.
Code Block
Below is a simple Python script of DLP using AI. Highlights of this Python script:
- This script provided in this example does not explicitly involve training data or a training phase because it uses a pre-trained language model (in this case, the en_core_web_sm model provided by spaCy) to perform content inspection based on patterns.
- This script defines a pattern to match credit card numbers using spaCy's Matcher class. This pattern is specified as a list of dictionaries representing the shape of tokens in the text. The Matcher class is then used to find matches for this pattern in the processed text.
- Additionally, this script uses a regular expression pattern to find credit card numbers in the input text. This regular expression pattern (\b\d{4}[-\s]?\d{4}[-\s]?\d{4}[-\s]?\d{4}\b) is used to search for sequences of digits that resemble credit card numbers.
- This script processes the input text using the pre-trained language model and searches for matches to the specified patterns (both using the spaCy Matcher and the regular expression). When a match is found, it prints out the identified sensitive information, such as credit card numbers.
import spacy
from spacy.matcher import Matcher
import re
# Load English language model
nlp = spacy.load("en_core_web_sm")
# Define a regular expression pattern for credit card numbers
credit_card_pattern = re.compile(r'\b\d{4}[-\s]?\d{4}[-\s]?\d{4}[-\s]?\d{4}\b')
# Load matcher for spaCy
matcher = Matcher(nlp.vocab)
pattern = [{"SHAPE": "dddd"}, {"SHAPE": "dddd"}, {"SHAPE": "dddd"}, {"SHAPE": "dddd"}]
# Define a pattern to match credit card numbers
matcher.add("CREDIT_CARD", [pattern])
# Sample text to inspect for sensitive information
sample_text = """
Hello, I am tim and my credit card number is 3434567890123956.
Please don't share it with anyone.
My email address is tim@example.com and my phone number is 613-468-7890.
"""
# Process the sample text using spaCy
doc = nlp(sample_text)
# Iterate over the matches found by the Matcher
for match_id, start, end in matcher(doc):
span = doc[start:end]
print("Sensitive information found:", span.text)
# Find credit card numbers using regular expression
credit_card_numbers = credit_card_pattern.findall(sample_text)
print("Credit card numbers found:", credit_card_numbers)
Sample Output 1
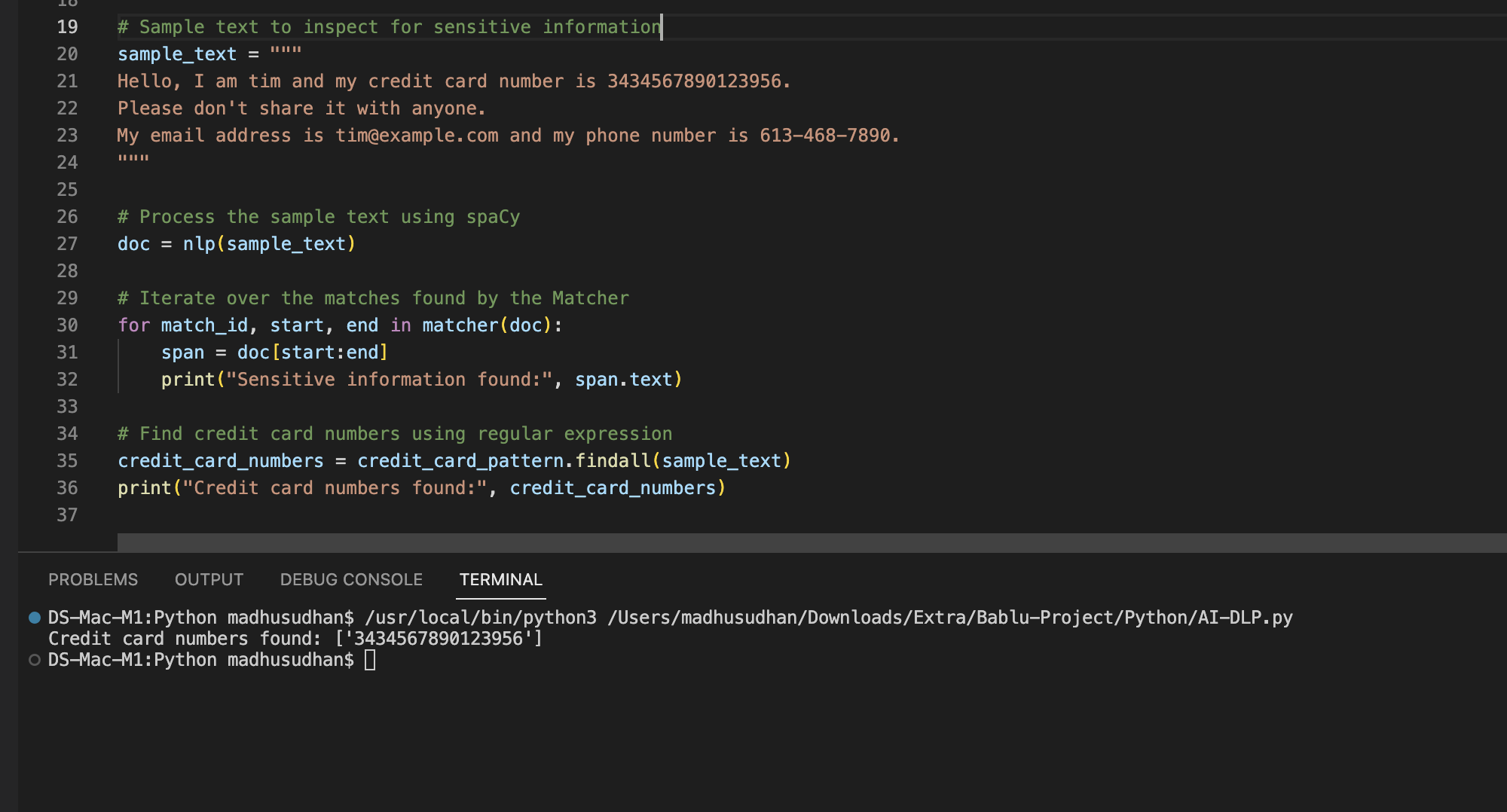
Sample Output 2
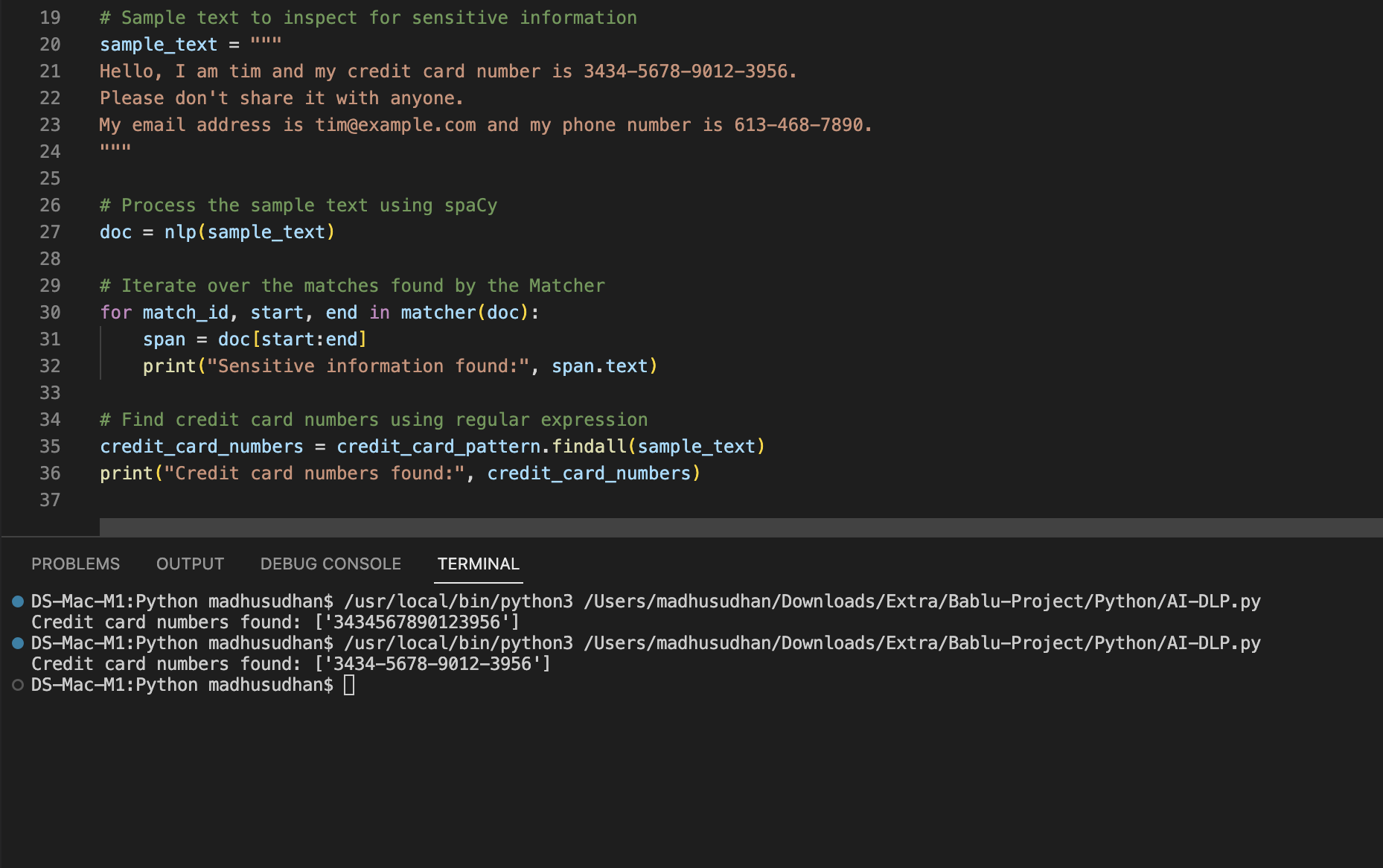
Conclusion
While this Python script demonstrates the use of AI techniques for content inspection, the efficiency and advantages of AI-based methods over traditional rule-based DLP methods depend on various factors, including the complexity of data, the accuracy requirements, and the specific use case. Organizations should evaluate different approaches based on their requirements and constraints to determine the most suitable content inspection solution.
Opinions expressed by DZone contributors are their own.

Comments