How to Implement Jenkins CI/CD With Git Crypt
Take a look at this tutorial that demonstrates how to implement Git secrets with a gpg private key and how to connect it with a Jenkins CI/CD pipeline.
Join the DZone community and get the full member experience.
Join For FreeSoftware applications are typically connected to externalities such as databases, SFTP sites, secured web APIs, etc. We often have to store the secrets used to access these externalities in the code we write and share these secrets with other developers in our team. These secrets can include things such as user IDs, passwords, private key files, or anything else that should not be seen by unauthorized persons. While the decision to include such secrets in a coding repository is often highly debated, there can be some use cases in which this approach may be necessary.
What Is Git Crypt?
git-crypt provides a security mechanism for Git repositories. It allows you to encrypt whatever files you wish within a repository. The encryption keys it uses can then be exported and securely shared among other developers, and it can be imported into tools such as Jenkins for testing and deployment.
Getting Started With Git Crypt
To get started with git-crypt, you will need to build it from a source or install it through your operating system's preferred package manager. Once that is done, you will need to initialize your (existing) repository to work with git-crypt:
$ git-crypt initYou then need to tell git-crypt which files it needs to encrypt. Say you have a file containing your secrets in a directory called secretdir and has the name i-want-this-to-be-private.txt. You would need to configure a .gitattributes file to tell git-crypt to encrypt this file:
# You can use the standard syntax of .gitattributes to configure this file,
# that could include things like wildcards or other directories.
secretdir/i-want-this-to-be-private.txt filter=git-crypt diff=git-cryptThe .gitattributes file
Once you commit the .gitattributes file, you will need to make and save a change to secretdir/i-want-this-to-be-private.txt so that it will need to be committed. Once you have committed the updated version of this file, it will be encrypted for the next developer who clones the repository.
You can use the git-crypt status command to verify that your file has been encrypted:
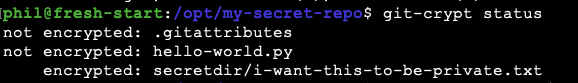
Another user who clones the repository and attempts to view the file without decrypting it will see gibberish:

One way to allow authorized users to work with the repository would be to securely share with them a key file that will give them access. You can export this key with the command; just make sure to not store it in the same directory as your repository:
$ # You can specify any file name or path here.
$ git-crypt export-key ../git-crypt.keyOnce another authorized user has the key, he or she can use it to decrypt the file and use the repository:
$ git-crypt unlock ~/git-crypt.keyNow that we have the export key, how do we integrate it into a Jenkins Pipeline?
How To Use Git Crypt in a Jenkins Pipeline
Creating Credentials in Jenkins
- Log into your Jenkins Web UI interface. Typically, this runs on port 8080 of the server on which Jenkins is installed.
- Within Jenkins, access the dashboard. Go to "Manage Jenkins." Then choose "Credentials."
- Upload the key you generated previously using the interface:
![Interface of uploading the key]()
- Use the added key file in the Jenkins Pipeline. Here "git-crypt-export-key" is the ID given when you add Jenkins credentials.
pipeline {
agent {
node {
label 'my-test-node'
}
}
environment {
mySecret = credentials("git-crypt-export-key")
}
stages {
stage("Decrypt the files") {
steps {
sh """
cd /opt/my-secret-repo
git-crypt unlock '$mySecret'
"""
}
}
}
}You may get a warning about data being passed insecurely by using this method.
Conclusion
This article shows us both how to use git-crypt to protect secrets in a Git repository and how to use the keys provided by the same for CD tools such as Jenkins.
Further Reading
Opinions expressed by DZone contributors are their own.


Comments