Master the Art of Data Security: A Complete Guide To Securing Data at Rest on Amazon S3
A guide to securing data at rest, this article explains the importance of data security, the potential consequences of unsecured data, and various encryption techniques.
Join the DZone community and get the full member experience.
Join For FreeAs we step further into the digital age, the importance of data security becomes increasingly apparent. Our interactions, transactions, and even our identities are frequently translated into data, which is stored, transferred, and processed in the digital realm. When this data falls into the wrong hands, the consequences can be disastrous, both for individuals and for organizations.
Amazon S3, a popular storage solution offered by Amazon Web Services (AWS), serves as a repository for a vast amount of this data. With its robust scalability and ease of use, it has become a favored choice for many organizations. But as with all data storage services, it's crucial to ensure that the data stored on Amazon S3 is secure, particularly when it's 'at rest'—that is, not actively being used or transferred.
Securing data at rest involves various methods, each one designed to protect your information from different types of threats. Amazon S3 provides several encryption options, including Server-Side Encryption with Amazon S3 Managed Keys (SSE-S3), Server-Side Encryption with AWS Key Management Service (SSE-KMS), Server-Side Encryption with Customer-Provided Keys (SSE-C), and client-side encryption. Each method comes with its own merits and considerations, which will be discussed in detail later in this article.
What Is Data Security on Amazon S3?
We've established the importance of data security in the digital era, but you might be wondering what this means specifically for Amazon S3. Well, data security on Amazon S3 is all about safeguarding your stored information from unauthorized access, loss, or theft. This involves implementing specific protective measures such as encryption methods and access controls, which we will explore further.
When we talk about 'data at rest,' we're referring to data that is not currently being transmitted or processed. It's essentially data that is sitting idle, stored in any kind of repository, like databases, data lakes, or, in our context, Amazon S3 buckets. Despite being inactive, it's crucial to secure this data. Why? Because it's often a prime target for cybercriminals, who can exploit vulnerabilities to gain access. The exposure of customer information, proprietary business details, or sensitive personal data could lead to severe consequences.
Why Is Data Security on Amazon S3 Important?
In the previous section, we looked into what data security on Amazon S3 entails. But why should we go to such lengths to secure data? Why does it matter so much? The importance of data security boils down to three primary factors: potential risks and vulnerabilities, legal and regulatory obligations, and the repercussions of a data breach.
The digital realm is fraught with dangers, especially for unsecured data. Cybercriminals are constantly probing systems, looking for vulnerabilities to exploit. Amazon S3, despite its robust security infrastructure, is not immune to these threats. If data stored on S3 is left unsecured, it becomes an easy target for bad actors. They can access sensitive information, manipulate it for nefarious purposes, or even hold it hostage through ransomware attacks. Therefore, leaving data unprotected on S3 is akin to leaving your house's front door wide open — it invites unwanted visitors.
Beyond the obvious threat of cybercrime, companies also have to contend with legal and regulatory mandates around data security. Numerous laws and regulations — like the General Data Protection Regulation (GDPR) in Europe, the California Consumer Privacy Act (CCPA) in the U.S., and many others worldwide — mandate that organizations must take proactive steps to secure their data. Non-compliance with these regulations can lead to hefty fines, not to mention a damaged reputation. Hence, ensuring data security on Amazon S3 is not just a best practice but a legal necessity for most organizations.
Imagine waking up one day to find out that sensitive data — customer information, financial records, intellectual property—has been stolen or manipulated. The consequences are devastating. A data breach can result in severe financial losses, erode customer trust, and even lead to business closure in extreme cases. Furthermore, individuals affected by such breaches can face serious privacy issues, identity theft, and potential financial loss.
In the grand scheme of things, securing data at rest on Amazon S3 is not just about ticking off a box on a cybersecurity checklist. It's about safeguarding your assets, reputation, and future. In the next section, I will delve into how exactly you can go about implementing these security measures on Amazon S3.
How To Secure Data at Rest on Amazon S3
Now that we understand the importance of data security on Amazon S3 let's delve into the practical side. We have four main encryption options for securing data at rest on Amazon S3: Server-Side Encryption with Amazon S3 Managed Keys (SSE-S3), Server-Side Encryption with AWS Key Management Service (SSE-KMS), Server-Side Encryption with Customer-Provided Keys (SSE-C), and Client-Side Encryption. Each of these methods offers a different level of control and responsibility.
SSE-S3 is a straightforward method where Amazon handles all aspects of encryption and decryption. When you upload a file, Amazon S3 encrypts it and stores the encrypted version. Whenever you access your file, Amazon S3 seamlessly decrypts it for you. This encryption method uses unique keys for each file and regularly rotates them for added protection. To enable SSE-S3, when you upload a file to Amazon S3, simply select the 'Server Side Encryption' checkbox in the 'Set Details' section.
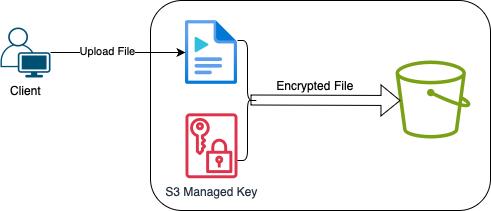
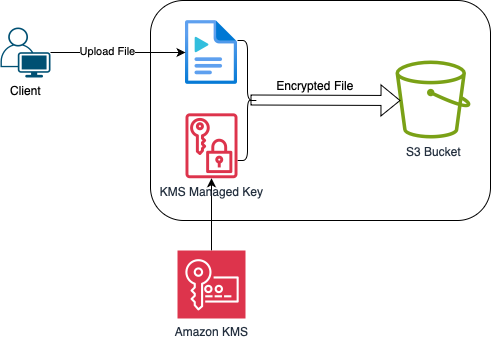
Moving up the complexity ladder, SSE-KMS provides an additional layer of security by allowing you to audit your key usage. AWS Key Management Service manages cryptographic keys for you, but you can track their use in a detailed fashion. This is particularly useful for organizations that need to maintain a stringent audit trail. For SSE-KMS, you will need to create a key in AWS KMS and then specify this key when you upload a file. SSE-KMS can also be configured as the default encryption method for an entire S3 bucket.
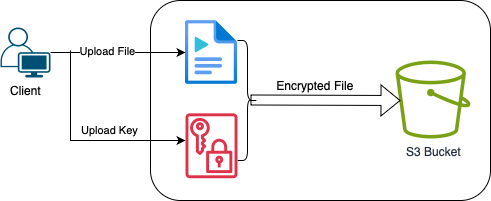
With SSE-C, you manage the encryption keys rather than Amazon. When you upload a file, you must also provide an encryption key. Amazon S3 uses this key to encrypt your file and then discards the key. When you access your file, you must provide the same key again. This gives you more control over your encryption keys but also adds to your responsibilities. For SSE-C, you must provide your encryption key with each upload and download request.
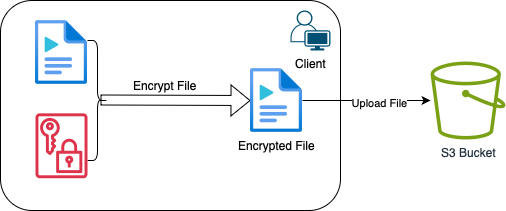
Finally, with Client-Side Encryption, you encrypt data on your side before uploading it to Amazon S3. This means Amazon S3 only ever sees the encrypted version of your data. You can manage keys yourself or use AWS Key Management Service. This option offers the highest level of control. For Client-Side Encryption, you will need to encrypt your files before uploading them. AWS SDKs include methods to help you do this.
Best Practices for Implementing Data Security Measures on Amazon S3
Regardless of the encryption method you choose, follow these best practices for securing data at rest on Amazon S3:
- Always encrypt sensitive data, whether it's at rest or in transit.
- Regularly rotate encryption keys where possible.
- Use multi-factor authentication (MFA) for deleting stored data.
- Enable logging and monitoring to detect any unusual access patterns.
- Follow the principle of least privilege: grant only necessary permissions and regularly review them.
In the end, securing data at rest on Amazon S3 is about understanding your security needs, choosing the right encryption option, and following best practices. Be proactive about your data security and stay ahead of potential threats.
Conclusion
In the digital age, where data is the new gold, securing this precious resource is paramount. We've journeyed through the importance of data security on Amazon S3, understanding not only what it entails but also its significance in today's world. We've explored the potential risks and consequences of neglecting data security, acknowledging the devastating impact a breach can have on organizations and individuals alike.
No organization or individual should underestimate the importance of securing data. The risk of breaches, coupled with legal and regulatory requirements, necessitates immediate attention to data security. Whether you choose SSE-S3 for its simplicity, SSE-KMS for a blend of control and convenience, SSE-C for full control, or Client-Side Encryption for maximum security, the important thing is to make a choice. Choose to protect your data; choose to secure your future.
As I wrap up this article, remember that implementing data security measures on Amazon S3 is not a one-time effort. Stay updated with emerging best practices in the field of data security. Regularly review and update your security measures to keep pace with evolving threats. Your commitment to data security is an ongoing journey, not a destination.
Opinions expressed by DZone contributors are their own.

Comments