Microservices With JHipster
In this article, we will be looking at the microservices stack that JHipster, a code generation tool, generates and supports.
Join the DZone community and get the full member experience.
Join For FreeJHipster is a code generation tool that can create web applications, microservices, deployment files for Kubernetes, cloud integrations, and CI/CD Jenkins files. This tool is very helpful for developers who can quickly generate the code and avoid creating a boilerplate code, which saves 30% of the effort.
JHipster supports back-end code in Spring Boot and front-end code in Angular/React/Vue.js.
In this article, we will be looking at the microservices stack that JHipster generates and supports.
Microservices are independent, modular deployable components split by business domain models, business functionalities that are scalable, efficient, and rapidly deployable.
Microservices are made up of several components including Service registry, Service discovery, Health check, Resiliency, Fault tolerance, and Security.
JHipster supports the following components for the Microservices to accomplish the above-mentioned components:
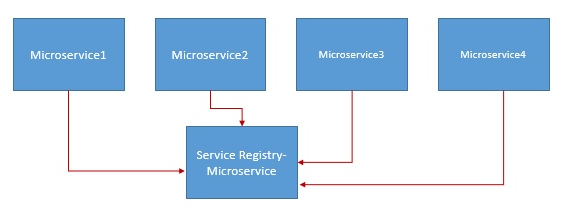
1. JHipster Registry: This is the service registry where different microservices can register and discover the configuration. The registry also provides monitoring and health check dashboards.
JHipster Registry is built on 2 components: Netflix Eureka and Spring Cloud Config Server.
a. Netflix Eureka: Eureka provides dynamic service registration and discovery. Eureka maintains a central service registry that can register the new microservices and delist the service when it goes down. The registry maintains up-to-date information on the services available and their metadata. The services that get registered to the Eureka server send their heartbeats and when the client no longer sends a heartbeat, the service is taken out of the registry.
Eureka provides dynamic discovery where clients look for the service registry to get the service information like the URL of the service and connects through the URL.
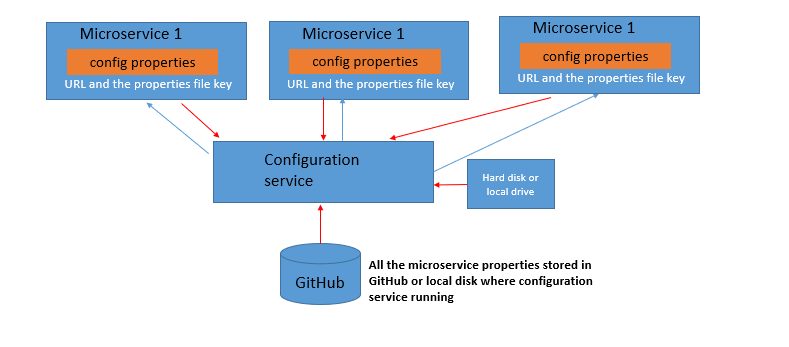
b. Spring Cloud Config Server: This provides the centralized store for managing the properties and configurations for all the microservices.
Microservice can connect to the cloud-config service and get the configuration details. The config service can also be exposed to a Rest API.
2. HashiCorp Consul: Consul is a service discovery client from HashiCorp. Consul provides service discovery, fault tolerance, vault for key-value storage. This is an alternative to JHipster Registry that can provide both service discovery and configuration store.
Eureka supports application services written in Spring Boot. Consul can support multiple clients written in Java, Golang, or other programming languages.
Consul supports multiple data centers out of the box. The node that runs Consul runs a consul agent that monitors the health of the service.
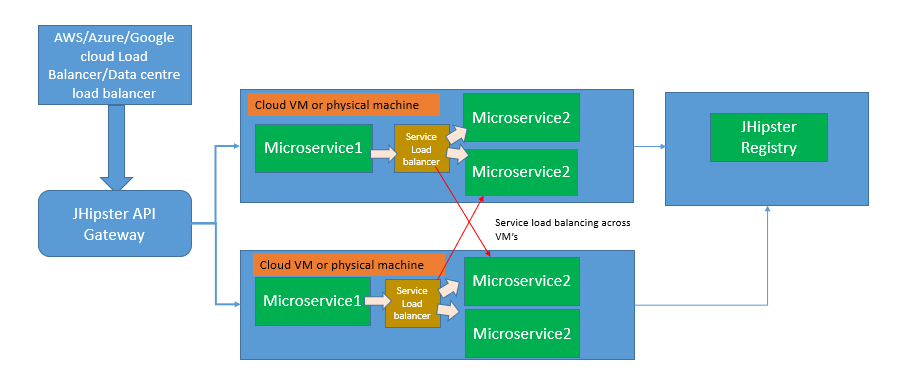
3. JHipster API Gateway
JHipster provides Gateway, which is the single point of entry for accessing the services. Gateway provides request, response transformation, API security, caching, throttling, routing, filtering, and fault tolerance.
JHipster gateway integrates with Zuul for API Gateway features and Hystrix for resiliency and circuit breaker features. As Hystrix support will be removed in the future, JHipster is looking for Resilience4J integration for circuit breaker features.
Hystrix or Resilience4J stops the cascading failures in distributed systems, enables fallback services, controls the latency of the system.
JHipster API Gateway will work with JHipster Registry for service discovery and load balance HTTP requests using Spring Cloud Load Balancer.
4. JHipster Control Center: The control center monitors and manages applications. The control center provides the following features:
a. Instances: Instances provide a list of application instances; when the service gets registered in the JHipster Registry, the service is available in the list of instances. It also provides a dashboard to view the list.
b. Metrics: The metrics are managed by a Micrometer that tracks system metrics like JVM, HTTP requests, cache usage, and database connections.
c. Health checks: The health checks are integrated with Spring Actuator to get the status of health of services.
d. Logs: Logs are integrated with Logback to trace the logs of the running application.
e. API documentation: API documentation provides Swagger APIn documentation.
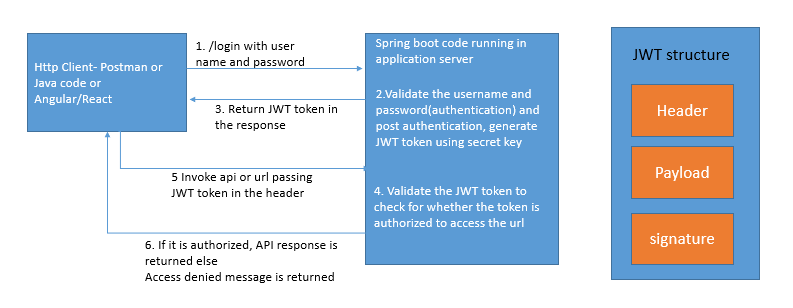
5. Security with JWT: JWT is a stateless security mechanism that can be scaled to multiple servers. This is the default security option for JHipster Microservices.
JWT provides Header, Payload, and Signature. All the client session data is stored in the token. No server-side session management is being done in JWT. JWT is supported by OAuth 2.0 for secure transmission.
6. Microservice Security with JHipster UAA: JHipster UAA is user accounting and authoring microservices using OAuth2.
OAuth2 is an authorization framework that can be used for centralized identity management. JHipster UAA provides an OAuth2 endpoint that provides access token based on the authentication. The token provides fine-grained access control to access the Rest based services. UAA is the combination of the authorization server and the resource server.
The sample OAuth flow depicted below:

The sample architecture stack generated for Microservices using JHipster is depicted below:
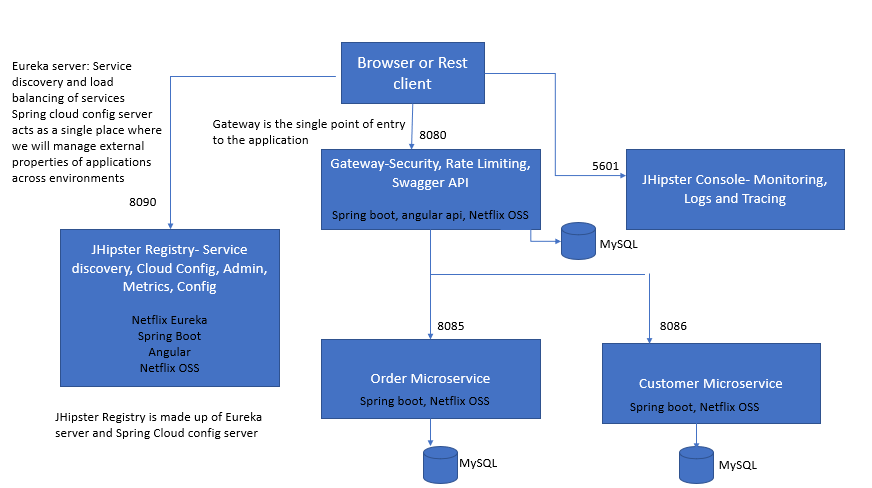
In this article, different microservices components supported by JHipster are described, which gives you an idea of how to build the Microservices stack using JHipster. Thanks for reading!
Opinions expressed by DZone contributors are their own.

Comments