What Is Threat Modeling?
Threat modeling is the engineering practice of reviewing the architecture and/or design of a system and its environment with the goal of identifying, prioritizing, and addressing potential security and privacy risks before they are exploited. Threat modeling, sometimes referred to as "whiteboard hacking," is a collaborative process where participants put themselves in the mindset of an attacker and analyze the system's design and architecture from an adversarial perspective, asking "what-if" questions with the goal of uncovering security risks and their potential impact.
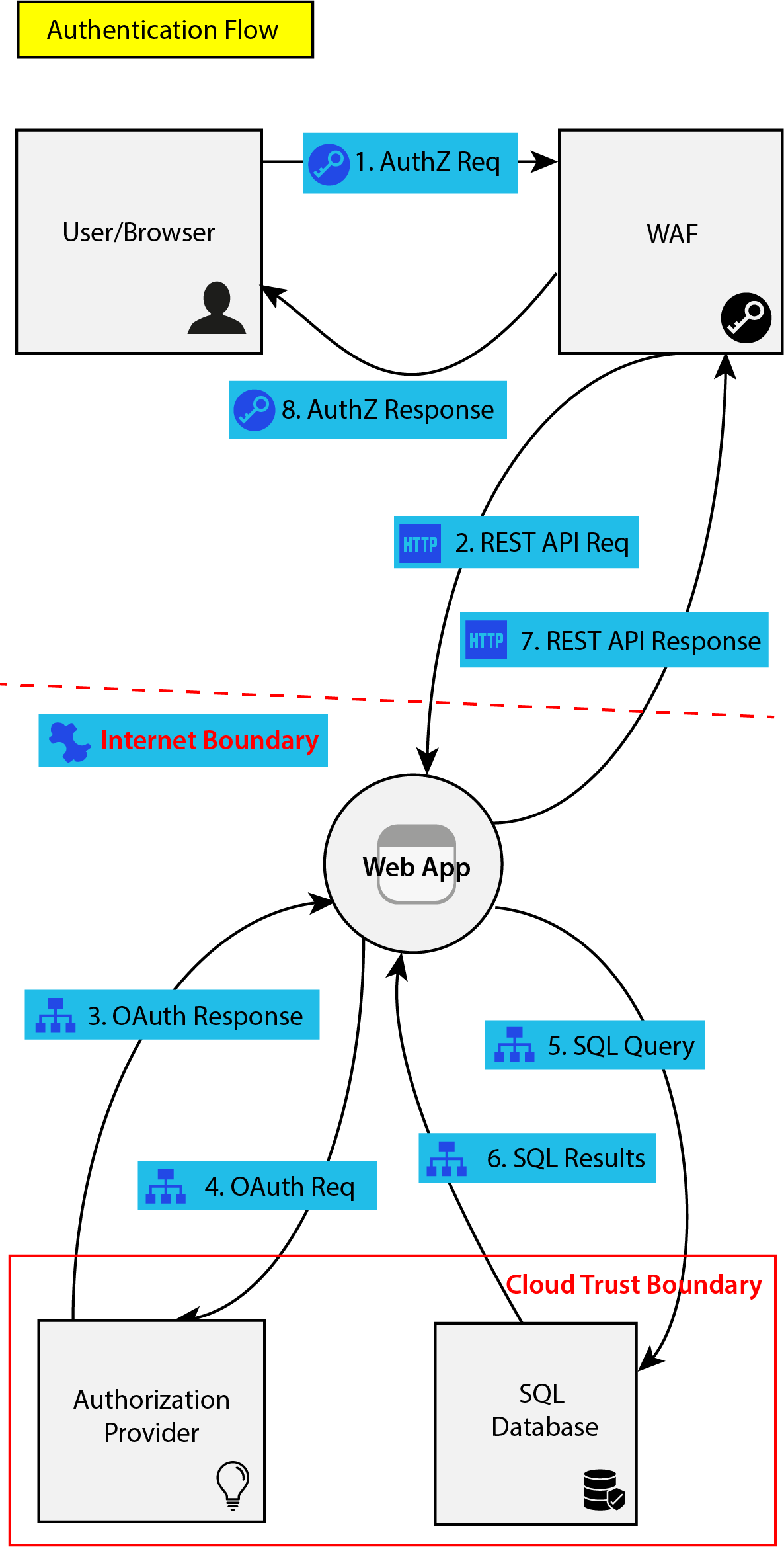
Threat modeling involves creating system models, data flow, and sequence diagrams of the under-review system, and documenting the attack surface, the threat actors, and the in-scope risks. If created manually, this process can create an additional workload for security and software teams, often delaying the release of software, creating friction between teams, and eventually becoming a tedious activity if it is not approached and managed properly. To address these challenges, the use of automation tools is becoming increasingly crucial, especially as the complexity of modern software systems grows due to numerous components, intricate interactions, and diverse trust boundaries.
Why Organizations Need Threat Modeling
Designing insecure software has always been a concern in software development; however, the complexity of modern software designs has amplified the problem. In 2021, OWASP recognized "insecure design" in its 2021 Top Ten list. Over the last few years, more and more standards and regulations have required organizations to systematically apply secure software design practices and threat modeling or security risk analysis processes. Standards such as the Application Security Verification Standard, IEC/ANSI 62443, and NIST 800-53/NIST 800-63/NIST 800-218 recommend threat modeling as a standard activity for every design change or sprint planning. Additionally, the recent US Government's Executive Order (EO) on Cyber Security requires organizations to prioritize software risk management efforts, including threat detection and analysis. With the increasing focus on security and regulatory compliance, organizations must provide evidence of the measures taken to ensure robust security throughout development.
Beyond standards and regulations, threat modeling enables organizations to determine the most appropriate and cost-effective security controls and countermeasures to mitigate identified threats as early as possible. Organizations often integrate threat modeling into their risk management process. This aligns security investments with potential security risks, optimizes resource allocation, and strengthens the overall cyber resilience strategy. It also provides a competitive advantage in the face of stricter regulations.
Threat modeling can also be a great way for organizations to "shift left" and to embark on a Secure-by-Design approach. By following a Secure-by-Design approach, organizations can incorporate suitable security controls into system designs preventing the higher costs that would result if these security gaps were only discovered during or after implementation, testing, or, worse yet, in production. This approach aligns with auditing and review requirements, as organizations can demonstrate the steps taken to ensure security from the outset of development.
Keys to a Successful and Secure SDLC
Gartner’s "Integrating Security Into the DevSecOps Toolchain" report suggests that threat modeling should be a core activity within the planning phase of the DevSecOps toolchain.
Treating security requirements and specifications for threat modeling as design activities gives security the same priority as other business and technical requirements that need to be addressed in the design stage, such as business logic, scalability, resiliency, testability, and efficiency. By considering security during the design stage, security controls can be integrated seamlessly into the architecture and environment of the software, reducing the likelihood of vulnerabilities being introduced later in the development lifecycle. Effectively, threat modeling during the design stage encourages cross-functional collaboration between security and software engineers/architects and product managers. This cross-team collaboration and shared understanding fosters a culture of security awareness, ensuring that security considerations are embedded throughout the SDLC. To achieve effective cross-team collaboration and communication of the identified threats, automation tools are also highly encouraged.
Threat Modeling Tools
Performing a threat model review is not an exercise that happens without proper preparation and background work. Software and security teams need to collaborate closely to define the threat modeling process, identify system assets, gather threat intelligence information, create threat modeling artifacts/diagrams, and log identified threats. Additionally, cyber security regulations and standards require organizations to demonstrate evidence showing conformance with the use of audit trail reports and dashboards. All of these pose challenges to software and security teams that could render the whole endeavor effectively impractical at a big scale if there were no tools to automate and streamline the threat modeling activities and processes.
Benefits of Threat Modeling Automation
Threat modeling tools allow software and security engineers to easily create and maintain data flow diagrams of their systems, regardless of their complexity and architecture. Without such tools, threat model reviewers would not be able to consistently capture all aspects of the ever-increasing attack surface of their software architectures.
Effectively, the way modern threat modeling tools manage the process allows all stakeholders to quantify the security risks and have better visibility, reporting, and understanding of the security posture of their systems.
Modern automation tools have:
- Simplified and accelerated the traditionally slow threat modeling processes by reducing time spent on repetitive tasks, resulting in substantial cost savings
- Simplified communication and improved collaboration between development and security teams
- Streamlined the threat modeling reviews and approvals workflows
- Ensured thorough attack surface coverage
- Created consistency in the way security findings are recorded, mitigated, and managed
- Allowed the threat modeling process and results to be more measurable
- Upleveled the overall quality of the process and security findings
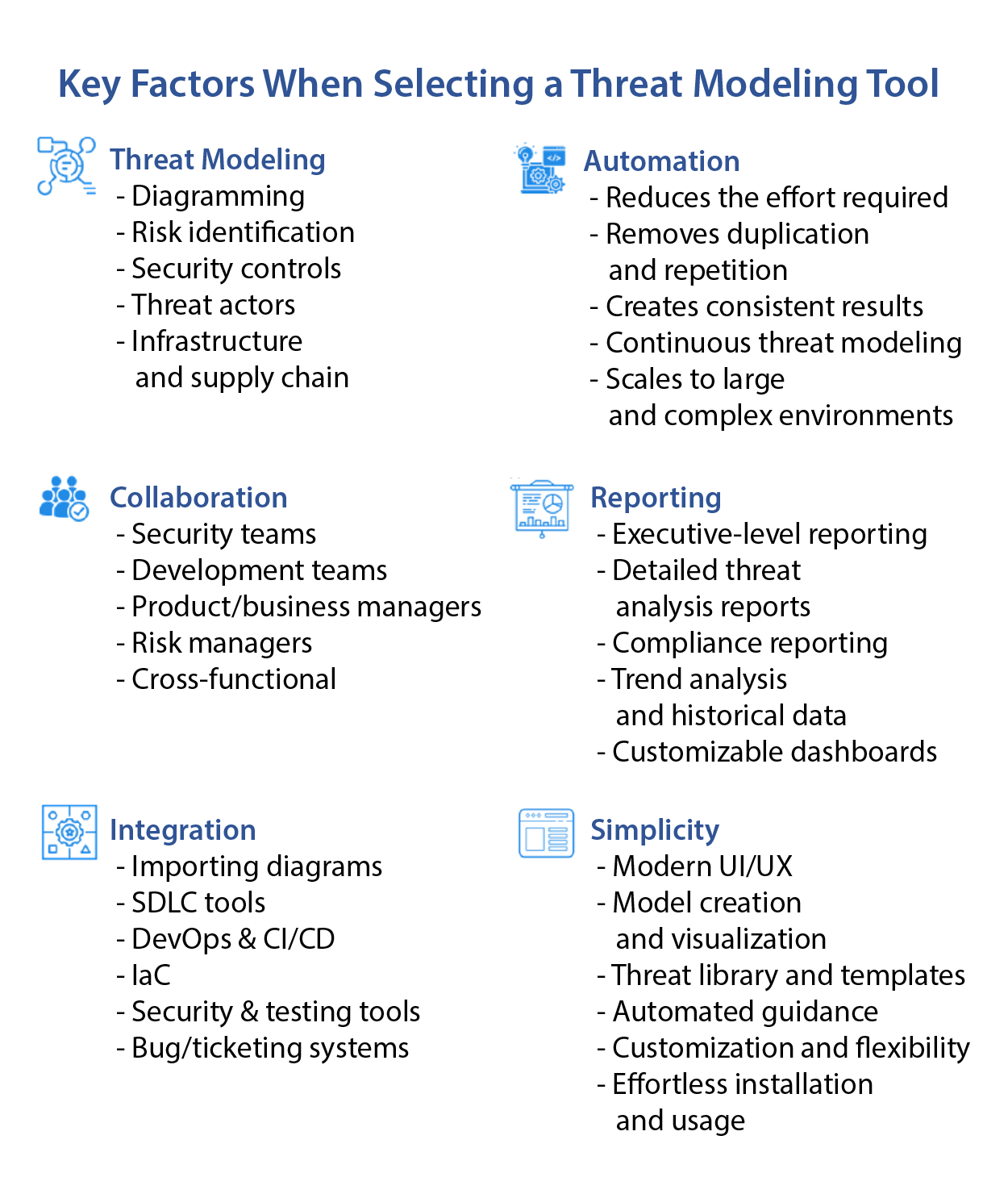
Selecting a Threat Modeling Tool
Selecting the right threat modeling tool involves considering key factors to meet organizational requirements. The most important factor is the tool's capabilities and ability to accurately identify security risks within a system with as few false positives as possible, taking into consideration its components, assets, trust boundaries, and attack surfaces.
Second, because security is not static, the tool should regularly update its security risk registry with newly identified threats and zero-days. Third, threat modeling tools should be compatible and integrate with the organization's existing architectural design tools to avoid duplication of designs and diagrams. For cloud-based systems that define their cloud resources via Infrastructure as Code (IaC), consider selecting a tool that can consume JSON/YAML resource files to further accelerate threat modeling of the system's cloud infrastructure. Additionally, integrating with DevOps tools and workflows for CI/CD facilitates automated threat model updates, saving additional valuable engineering time and accelerating threat modeling.
To facilitate the management of security findings within the SDLC, emphasis should be placed on the tool's integration capabilities with issue-tracking systems and collaboration platforms. This integration is critical for the overall user experience and promotes efficient teamwork.
Finally, when performing threat modeling at scale, there will be challenges around handling, analyzing, alerting, and reporting security findings. Thus, organizations should consider the threat modeling tool's capabilities on data analytics, reporting, custom dashboard creation, and compliance adherence against open standards such as the OWASP ASVS.
Figure 1: Key factors when selecting a threat modeling tool


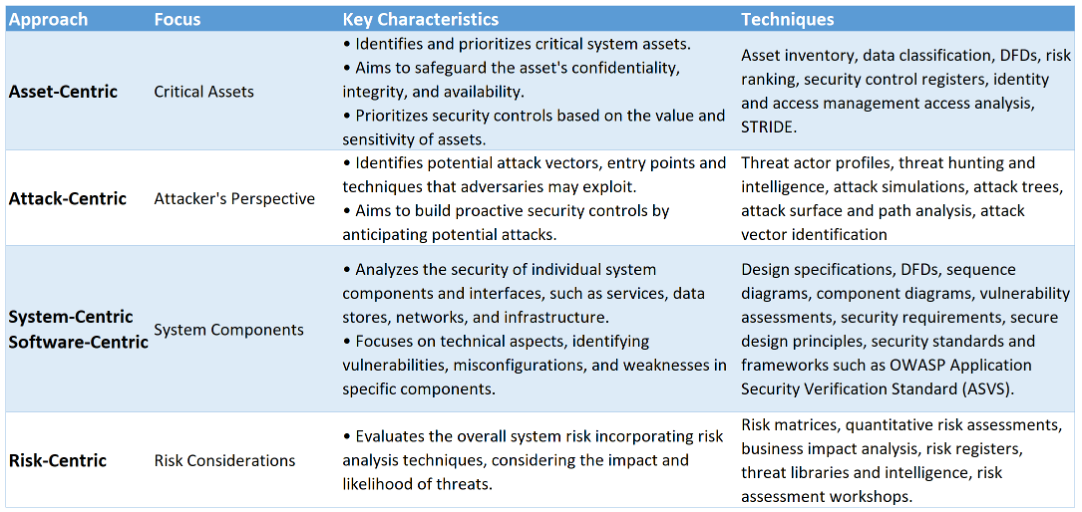
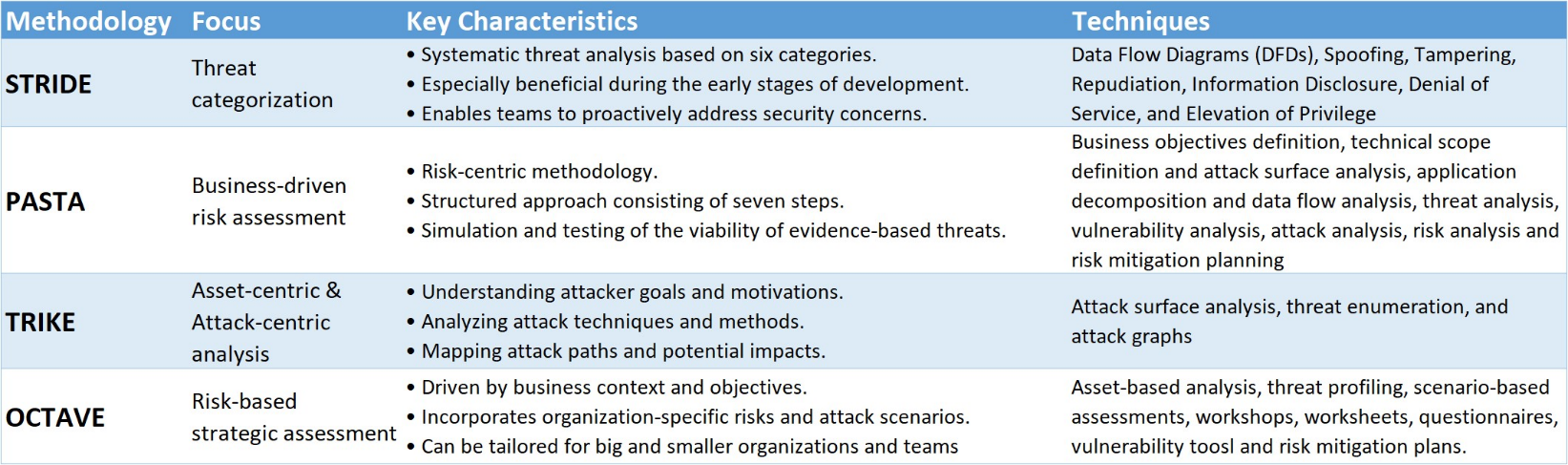
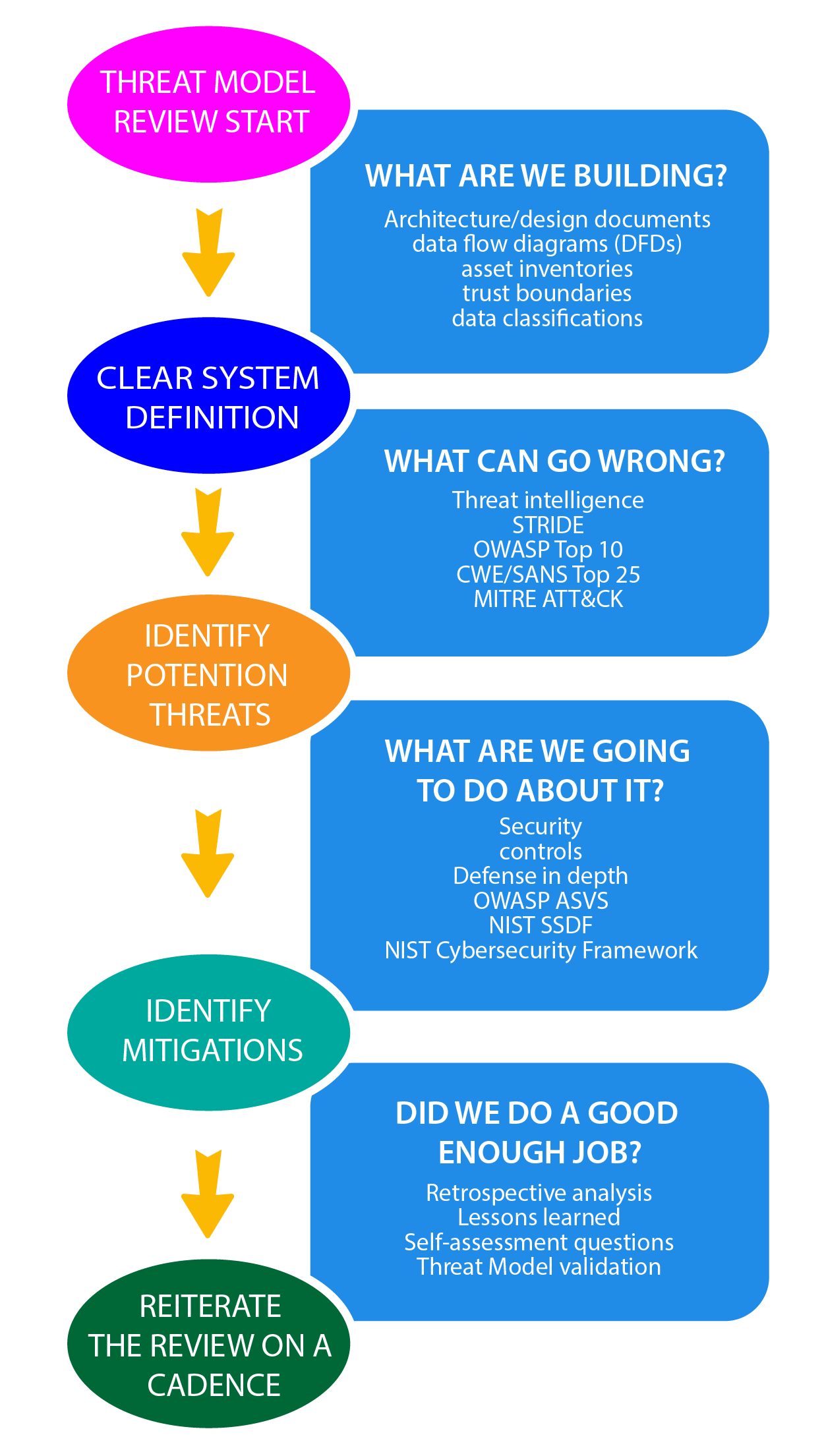
 Assessing and Documenting Identified Threats
Assessing and Documenting Identified Threats
{{ parent.title || parent.header.title}}
{{ parent.tldr }}
{{ parent.linkDescription }}
{{ parent.urlSource.name }}