Top 4 Developer Takeaways From the 2024 Kubernetes Benchmark Report
The 2024 Kubernetes Benchmark Report contains some key findings with implications for developers in the areas of cost efficiency, reliability, and security.
Join the DZone community and get the full member experience.
Join For FreeWe already know that Kubernetes revolutionized cloud-native computing by helping developers deploy and scale applications more easily. However, configuring Kubernetes clusters so they are optimized for security, efficiency, and reliability can be quite difficult. The 2024 Kubernetes Benchmark Report analyzed over 330,000 K8s workloads to identify common workload configuration issues as well as areas where software developers and the infrastructure teams that support them have made noticeable improvements over the last several years.
1. Optimize Cost Efficiency
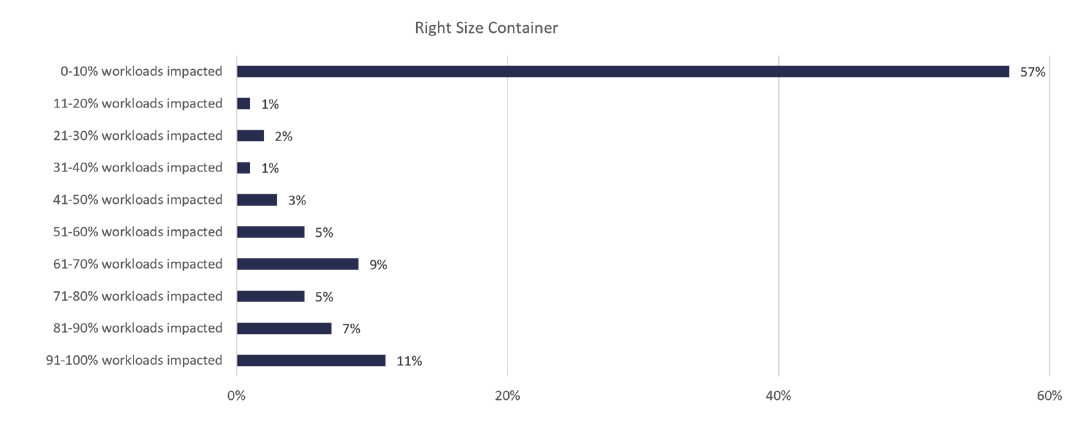
Efficient resource management is key to optimizing cloud spend. The Benchmark Report shows significant improvements in this area: 57% of organizations have 10% or fewer workloads that require container right-sizing. Software developers can use open-source tools such as Goldilocks, Prometheus, and Grafana to monitor and manage resource utilization. Appropriately setting CPU and memory requests and limits helps developers prevent resource contention issues and optimize cluster performance. Right-sizing means increasing resources to improve reliability or lowing resources to improve utilization and efficiency based on the requirements of each application and service.
2. Improve Reliability
Reliability is critical for applications and services running in any environment. One configuration issue that can seriously impact the reliability of workloads is when workloads are missing liveness and readiness probes. The benchmark shows that 69% of organizations have between 11-50% of workloads missing liveness probes, while 66% have the same percentage missing readiness probes. Developers must configure these probes to ensure that their applications and services continue to work properly if a container failure occurs.
3. Prioritize Security
Kubernetes is not secure by default, which means setting configurations correctly is particularly important. Workload misconfigurations can result in vulnerabilities, opening an attack vector for malicious actors. The benchmark indicated that security remains an area of concern, as 28% of organizations have more than 90% of their workloads running with insecure capabilities. Similarly, analysis showed that 44% of organizations ran 71% or more of their workloads with run as root access allowed. There are a lot of best practices related to security configurations that software developers should be making in order to improve the security of workloads.
Identify Image Vulnerabilities
Since the emergence of Docker, image security has been a concern because outdated or vulnerable container images can pose significant risk, particularly in the case of known vulnerabilities. Analysis revealed that 30% of organizations had more than 90% of workloads impacted by known vulnerabilities. Regularly scanning for image vulnerabilities using solutions such as Trivy or using Base Image Finder to detect which base images were used to build the container (and whether the base image needs updating) can help you minimize the number of vulnerable images in use, provided you patch vulnerable container images once they have been identified. Finding and remediating image vulnerabilities helps software developers minimize security risks and improve the reliability of applications.
Implement Network Policies
Network policies play a vital role in securing Kubernetes clusters. Given the importance of these policies, it was surprising to find that 58% of organizations were missing a network policy on more than 50% of their workloads. On the positive side, 37% of organizations had 0-10% of workloads impacted by this issue. Implementing network policies to control pod network communication and preventing unauthorized access to external resources is an excellent way to improve container security. Polaris is an open-source policy engine that includes checks to verify whether you have these policies (and many others) in place.
The analysis of workload security in the benchmark underscores the need for software developers to implement and automatically enforce strong security policies and configurations.
4. Harden Kubernetes Environments
The National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) provide a guide to hardening Kubernetes to help organizations manage Kubernetes-related risks and take advantage of Kubernetes technology without compromising security. This year, the Kubernetes benchmark included NSA Hardening Guideline checks, making recommendations for hardening Kubernetes clusters and outlining a strong defense-in-depth approach. The benchmark data showed that 33% of organizations have more than 50% of workloads with excessive privileges allowed, highlighting another area for improvement in the year ahead.
Compare to the 2024 Kubernetes Benchmark
Developers trying to find ways to improve the security, cost efficiency, and reliability of their Kubernetes clusters benefit from reviewing the latest benchmark report. It shows areas that remain a challenge for most organizations in terms of Kubernetes workload optimization as well as which areas have improved over the last three years. Review the benchmark and use some of the free and open-source solutions available to help you evaluate your own Kubernetes workloads and improve workload configurations.
Opinions expressed by DZone contributors are their own.

Comments